In this blog post i’ll share with you a resolution of an issue i was stumbling across, which cost me a full working day, hopefully this will spare you some troubleshooting time.
The Scenario
While building a setup
the certificate authority (CA) includes a Windows 2016 server PKI structure with 2 CA servers, the root CA called K3 and the subordinate intermediate CA called K4. the goal is generating the certificate signing request (CSR) on the AP itself without using any external tool like OpenSSL.
First try
Generated the CSR in the AP and signed it using a user template in the web enrollment tool of the CA.
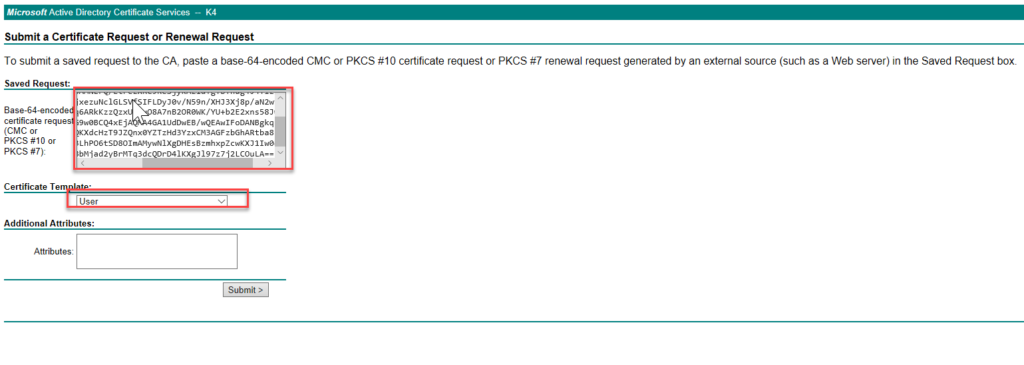
wgb-01(config)#CRYpto pki enroll WGB-TLS
% Start certificate enrollment ..
% The subject name in the certificate will include: CN=wgb-01
% The subject name in the certificate will include: wgb-01.lab.local
% Include the router serial number in the subject name? [yes/no]: yes
% The serial number in the certificate will be: FGL1864XD94
% Include an IP address in the subject name? [no]: no
Display Certificate Request to terminal? [yes/no]: yes
Certificate Request follows:
MIIBpzCCARACAQAwRjEPMA0GA1UEAxMGd2diLTAxMTMwEgYDVttFEwtGR0wxODQ2
WEQ5NjAdBgkqhkiG9w0BCQIWEHdnYi0wMS5sYWIubG9jYWwwgZ8wDQYJKoZIhvcN
AQEBBQADgY0AMIGJAoGBAMNEFQ/EtFezXRC9ReSjyKAz1dTgTB+nug4J4TlziJWF
K9NcwBapjPqmvCZ5QFnjxezuNclGLSVfSIFLDyJ0v/N59n/XHJ3Xj8p/aN2wvMVQ
LYyXqdf0ThRF0vgIv72q6ARkKzzQzxUzBuO8A7nB2OR0WK/YU+b2E2xns58JwD1J
AgMBAAGgITAfBgkqhkiG9w0BCQ4xEjAQMA4GA1UdDwEB/wQEAwIFoDANBgkqhkiG
9w0BAQUFAAOBgQArS3JQKXdcHzT9JZQnx0YZTzHd3YzxCM3AGFzbGhARtba832JU
+sbgIwWjOx1yvGuldwB3LhPO6tSD8OImAMywNlXgDHEsBzmhxpZcwKXJ1Iw0qftO
G1rkdduor73Qa742PhkBbMjad2yBrMTq3dcQDrD4lKXgJl97z7j2LCOuLA==
---End - This line not part of the certificate request---
Redisplay enrollment request? [yes/no]: no
Issue 1
despite the fact in the CSR a CN=WGB-01 is defined in the subject name, after signing the certificate
Second try
reviewing the certificate template on the CA server revealed the source of this behavior. the template instruct the CA to use the AD user information.
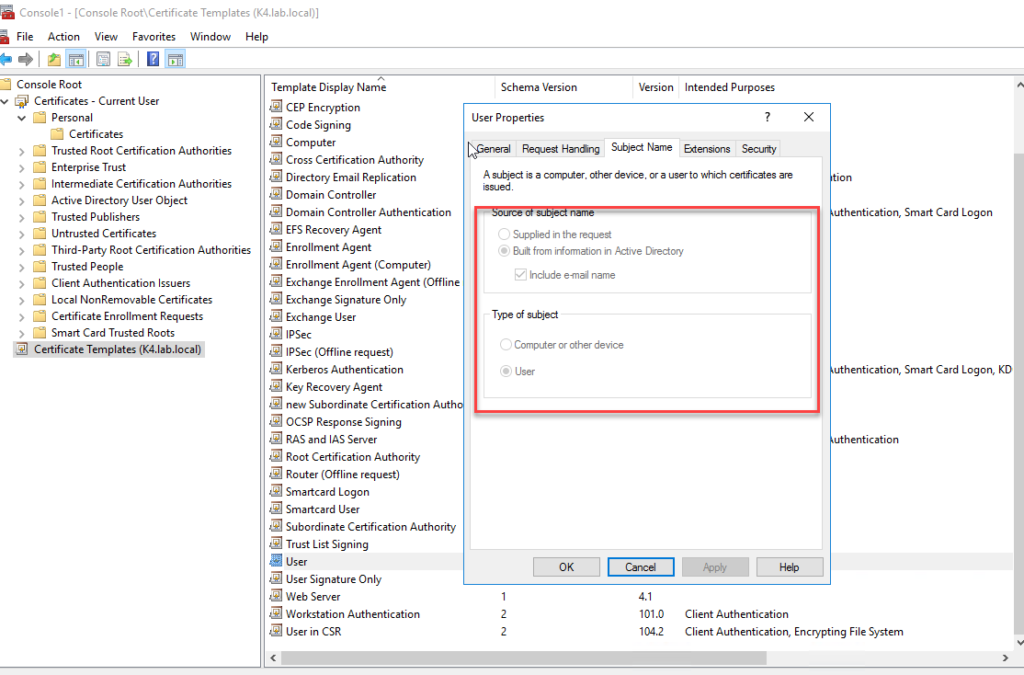
immediately after finding my mistake,
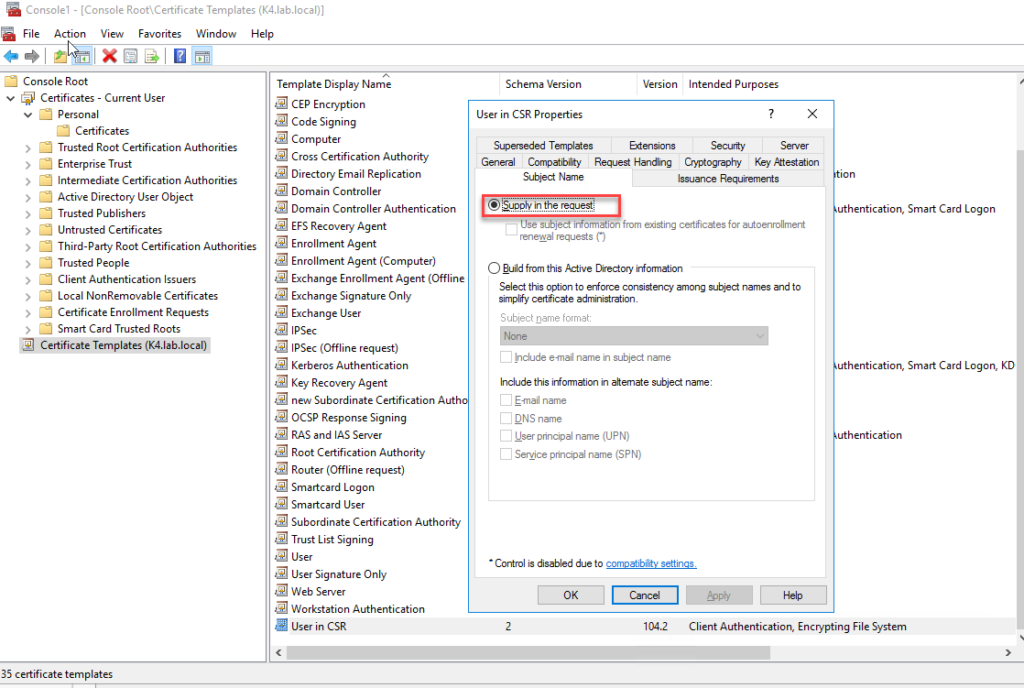
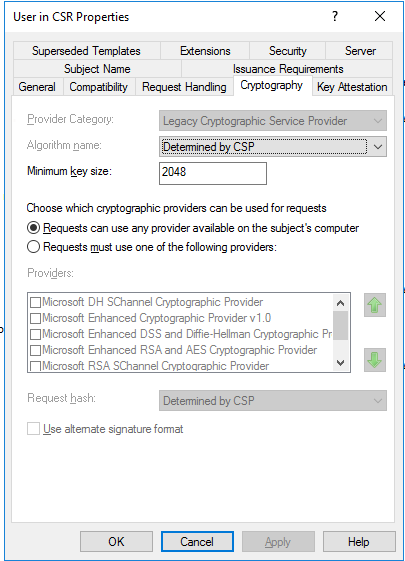
another important piece of information in this template is the encryption key size, which is set to 2048. taking this as granted had cost me the majority of time troubleshooting issue 2, and I’ll explain.
Issue 2
back to the
Your Request Id is 21. The disposition message is "Denied by Policy Module".
wait a minute, sure, this is a Cisco AP version 15.3(3)JD4 now can it be this AP generate a 1024bit key CSR by default? sure it is.
Resolution
changing the CSR key size in Cisco AP is how was this issue fixed, commands:
wgb-01(config)#crypto pki trustpoint WGB-TLS
wgb-01(ca-trustpoint)#rsakeypair wgb-01 2048
please help me to improve writing by feedback!