for the purpose of this post I assume that you have a Windows server already installed and running in your environment. in our lab we have one VM serving multi-role included Active Directory, DNS server, and Certificate Authority.
also the client computer is not enrolled in the AD, therefore, we need to manually request a certificate and install it on the computer that connecting to the 802.1X secured Wlan.
get the client certificate:
1- go to https://{CA-name or IP address}/certsrv
when prompt for credentials use the Active Directory username and password.
for example: https://172.16.1.1/certsrv/
2- click on request a certificate, then user certificate at the next screen.
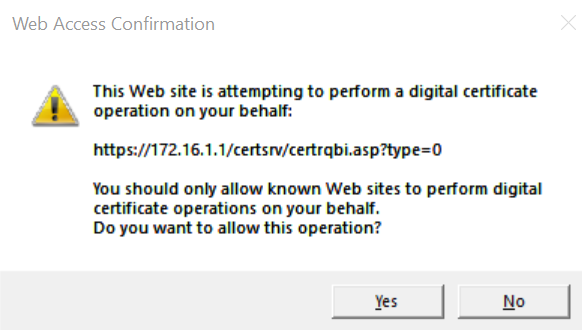
depends on the browser settings, a dialog box might ask for confirmation, click yes. then click submit.
now the web enrolment services will submit a certificate signing request, the CA in return will sign it. the result is a client certificate.
I’m planning to use the certificate on my test laptop, the next step is to click on install this certificate.
if you have reached this stage without any errors then good job, now try to connect to your 802.1X wireless network.
I have encountered some errors during this process of installing a CA from scratch, some of them related to the server configuration and others related to the browser.
Issue Nr.1
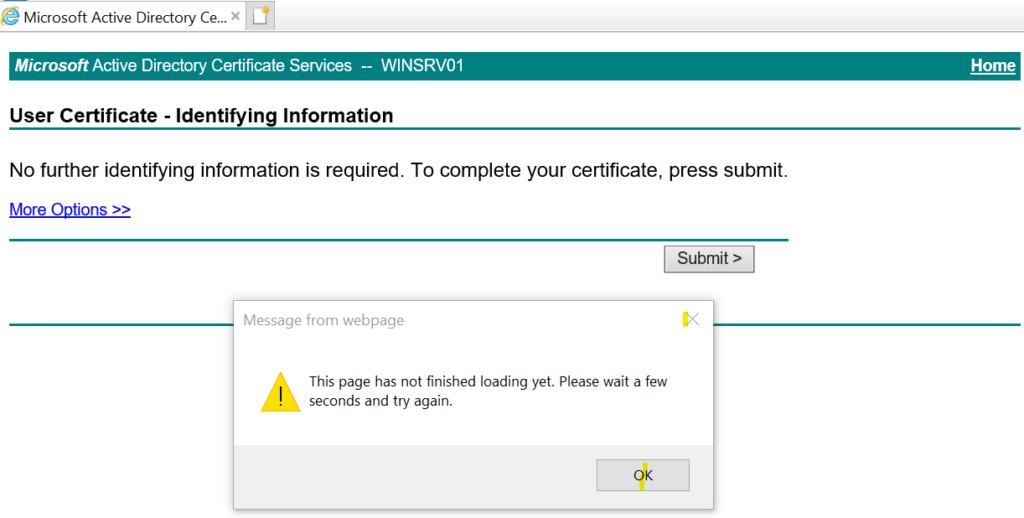
for example when submitting the certificate request, a dialog appears saying “this page has not finished loading yet. Please wait a few seconds and try again.” so I waited!
waiting didn’t solve the problem, what really did was enabling “Active scripting” in Internet Explorer settings. to do so:
Open Internet Explorer >> go to Internet options >> security >> chose the zone >> click custome level.
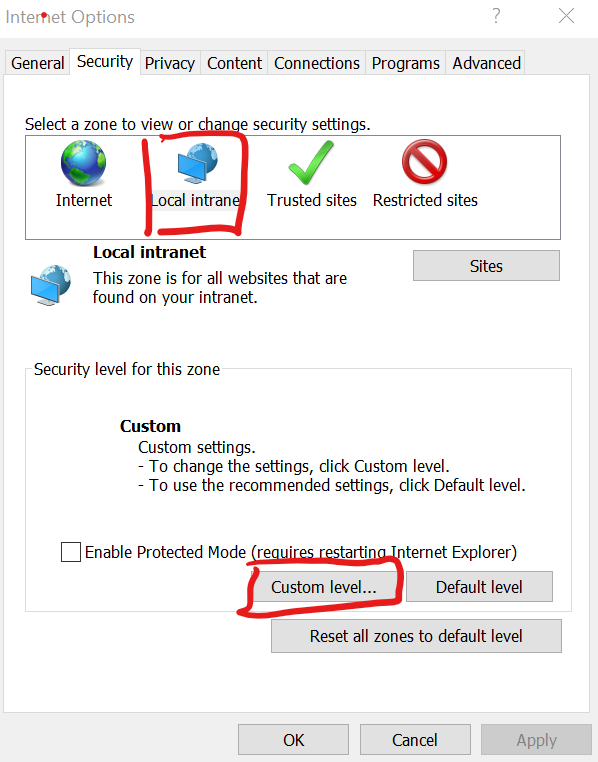
scroll down to “scripting” and select enable “active scripting”
Issue Nr.2
you might see another error message when submitting the request, primarily when using google chrome.
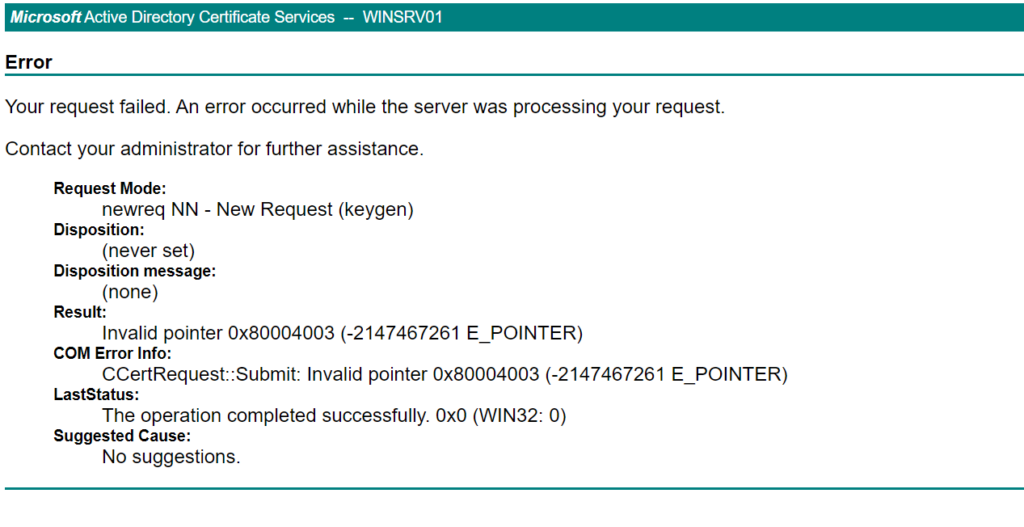
to fix this problem some configuration need to adapted on the CA side, more specifically on the IIS server which hosting the the Certificate enrollment service. lucky me this time, it is all in on the same server.
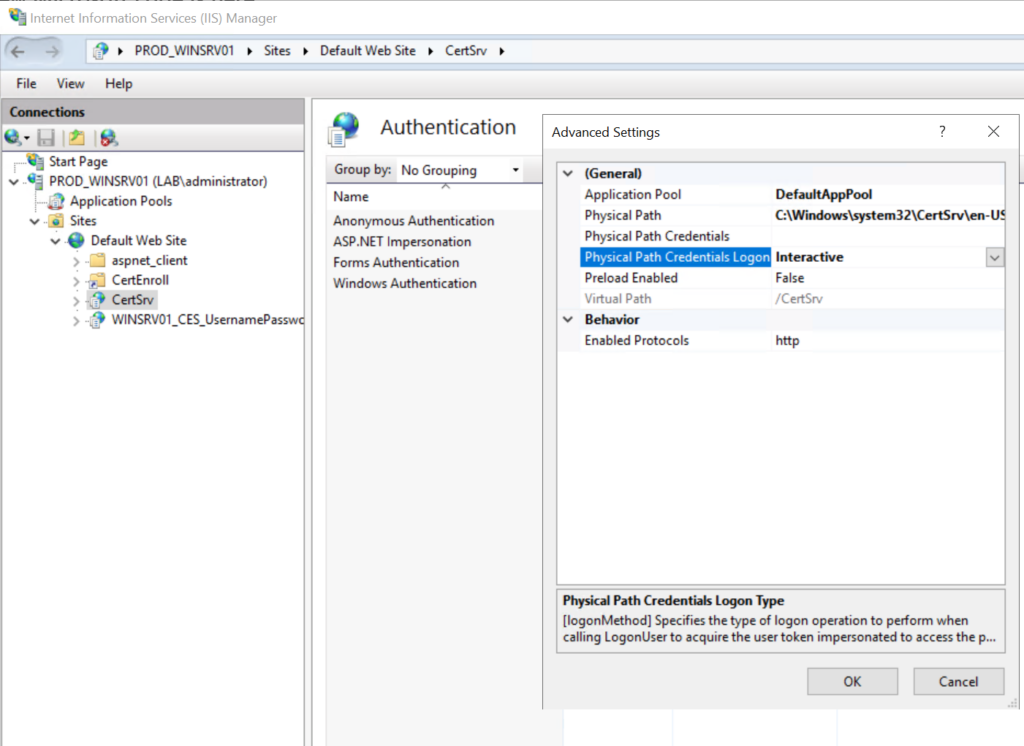
now go open your IIS Manager and click the server name, navigate to authentication and make sure Anonymous authentication is disabled, and Windows authentication is enabled.
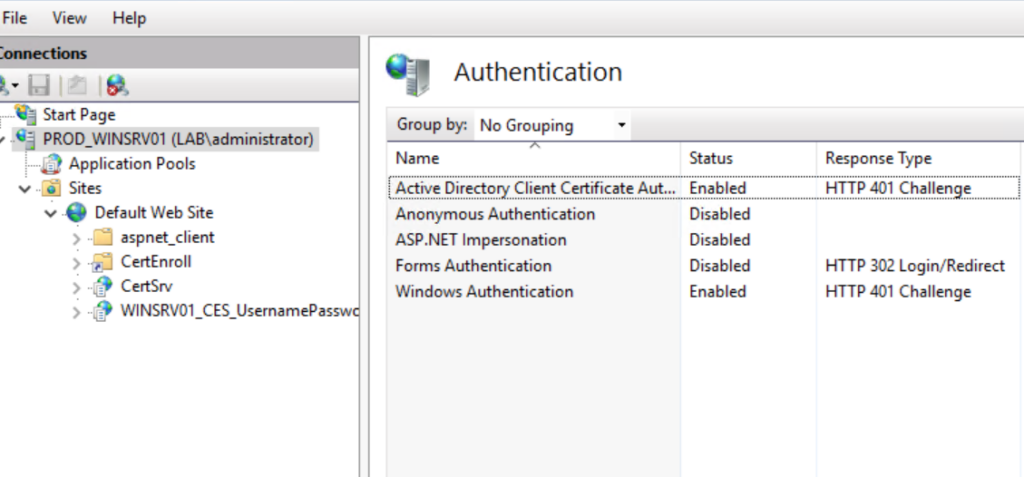
repeat the former step also for the “Default Web Site” and for “CertSrv”. when this is done, write click on CertSrv >> Manage Apllication>> Advanced settings, and change the “Physical Path Credentials Logon” to Interactive.